By Dimi Sandu, Head of Solutions Engineering (EMEA)
With IT and facilities converging, it is essential for any security professional to understand, on a high level, the way the LAN (Local Area Network) works. This will allow them to plan and secure their deployments in a more redundant manner, working alongside their IT colleagues and technical integrators in order to improve the overall system.
In this article, I will list the most common elements making up the LAN, the infrastructure that not only allows employees to work, but also connects all IT systems, including the security devices (e.g. IP cameras to NVRs).
1) WiFi Access Points
WiFi access points allow for wireless connectivity, mostly used for end users’ computers and phones. They are often found on ceilings or walls, installed in plain sight, as hiding them reduces/attenuates the signal, directly impacting the quality of the connections.
A well-designed wireless network must cater not only for speed, but should also reach all the areas of the building. Furthermore, detailed capacity planning must happen, in order to prevent degraded performance caused by spikes in traffic or increased volume of clients (e.g. during working hours or in a busy area, such as an amphitheater during a conference).
Many other things can negatively affect the service, including devices that create interference (e.g. microwave ovens) and obstructions (usually metal objects and concrete or glass infrastructure).
Because of the lower reliability of the wireless network, it is usually not used to connect to security devices, with administrators and vendors alike preferring a wired (thus more stable) connection. In addition, small devices such as CCTV cameras, do require power to be supplied, and this usually happens over the same wire as used for transmission.
2) Switches
If a device has a wired connection to the Internet (e.g. printers, servers, computers, and even access points - we call these end devices), most likely it is connected to a switch. Switches come in many shapes and sizes, one of the most common differentiators being the number of ports they have (can run from 4 to over 48). Their main task is to aggregate/connect to all the end devices (considered downstream) and switch the data between the source and the destination.
A simple example would be that of a laptop and printer, both connected via wires to the same LAN. In this case, the switch (or switches) job is to get the data from the source (laptop) to the destination (printer), where it will be interpreted and then processed (or printed). This can also happen if both devices are connected wirelessly, with the switches directing traffic from the source access point to the destination one and vice versa.
Although the number of ports is one of the differentiators when it comes to cost, some switches do command a premium, due to extra software and hardware features (such as redundant power supply options, or the ability for the switch to provide power to downstream devices).
Most switches today come with the option of providing power to downstream devices via a protocol called PoE (Power over Ethernet, read more here), which comes in a few different flavors (depending on the power provided). This comes in use not only when powering access points and IP phones, but also IP cameras and sensors.
3) Routers and firewalls
Going up the pyramid, switches connect to routers, the latter being responsible for directing traffic between the devices in the local area network, or between them and the rest of the Internet. As opposed to a switch, routers tend to have fewer ports, as their main job doesn’t (usually) include connecting to end devices. However, the routers tend to be much richer when it comes to the software components that allow them to forward/route traffic as fast and efficiently as possible.
In a medium to large size LAN, the number of routers is smaller than the number of switches (thus the pyramid visualization), but in the case of very small networks, both functions can combine in one device (e.g. the broadband router most people have in their homes).
Firewalls are devices that perform all sorts of security functions, from blocking unwanted traffic to acting as a network anti-virus and performing content filtering and application blocking (in this role they are also known as UTMs, or Unified Threat Managers). Although traditionally they have been a separate device, these days they are integrated into routers or offered as a cloud service, most of the time connecting the trusted LAN to the wider untrusted Internet (known as the WAN or Wide Area Network).
As a side note, a business will own and be responsible for its LAN (can be managed in house or via a contract with a technology integrator), while the WAN is the collection of service provider networks that allow for multiple LANs to communicate (e.g. multiple offices belonging to the same entity, requiring to exchange data).
A router/firewall connected to the Internet will have a few physical ports dedicated to the LAN (usually connected to the switches downstream), and a couple for the upstream, linked to the ISP (Internet Service Provider) lines. Smaller devices, typically deployed at the branch, will also optionally come with one or two SIM card slots, to allow for cellular backup.
4) Cellular Routers
Although this could be part of the above section, cellular routers do deserve a place of their own, especially with the increased use and availability of technologies such as 4G (also known as LTE) and 5G.
In some cases, the cellular router is a function of the main branch routers, however, in certain cases, there is a need to deploy a separate device and dedicate it for this sole purpose.
It can come with different options, catering for multiple SIM cards, and different types of external antennas that can be installed outside the facility (by extending the cables between the device and antenna or placing the whole device outdoors, if ruggedized - insulated from the effects of water and dust), and the ability to route across multiple circuits at the same time.
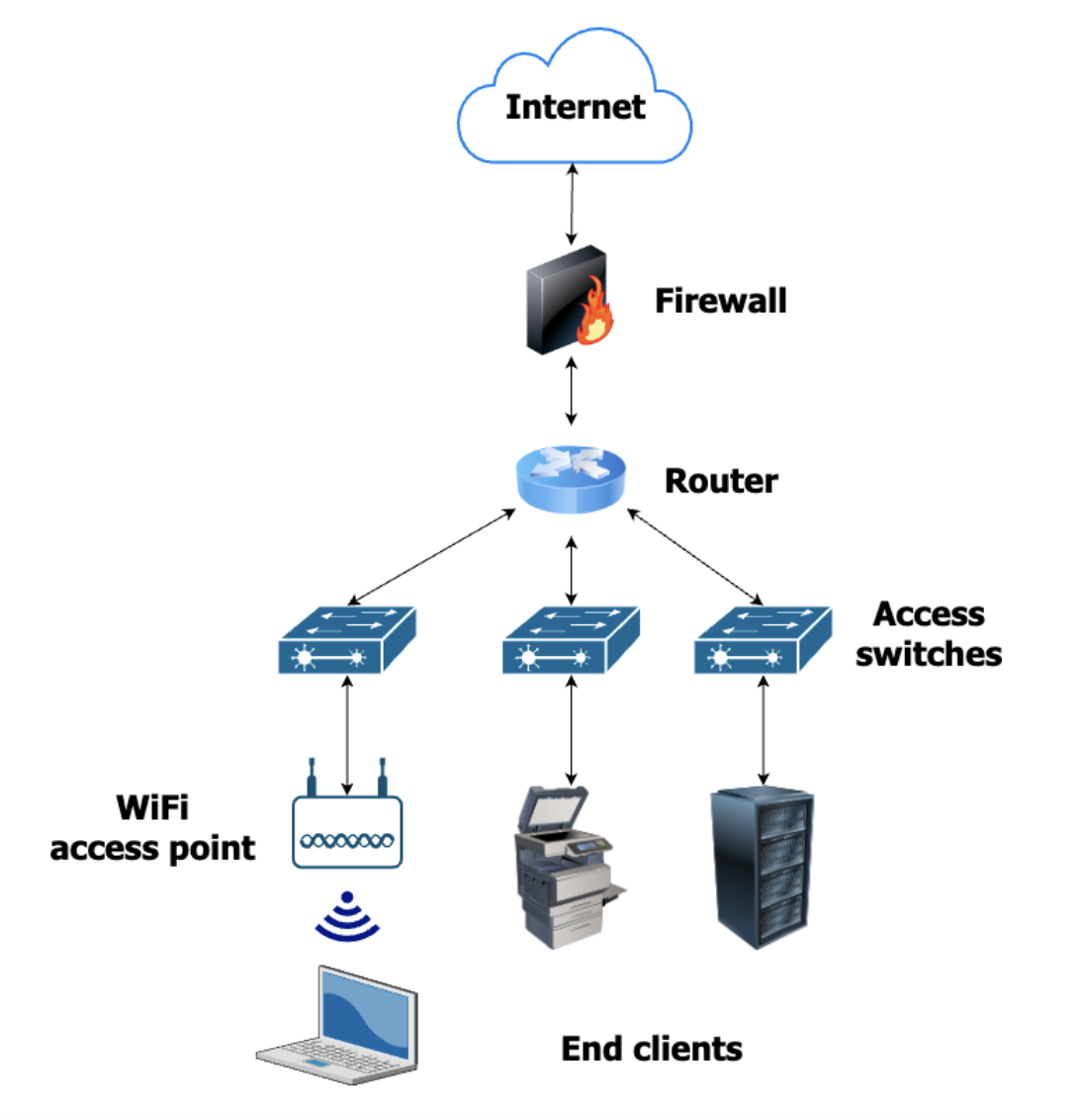
Diagram: a simplified depiction of different end devices connected to the LAN
For more videos on physical security & networking, follow Dimi on his YouTube channel: https://www.youtube.com/c/DimitrieSanduTech