By Dimi Sandu, Head of Solutions Engineering (EMEA)
Overview
For communication of potentially sensitive information, encryption methods are crucial for protecting confidentiality.
Today, most encryption is done on the devices we use each day, made possible because of advances in hardware and software. At its core, encryption is achieved by scrambling data using a cryptographic key, only known by the sender and the receiver. A third party would be aware of the conversation, but not able to interpret it.
Symmetric Encryption
The easiest way to achieve encryption is using a symmetric key algorithm, where both the sender and receiver share the same key, the former using it to encrypt, and the latter to decrypt. One common such algorithm is AES (Advanced Encryption Standard), used in VPN tunnels between different enterprise locations, critical in maintaining privacy when using public transmission networks such as the Internet. The AES notation is usually followed by a number (e.g. 128, 192, 256), denoting the length of the key, in bits. The longer the key, the harder it would be for an attacker to decrypt the message using brute force methods (trying every combination).
Symmetric encryption requires an administrator to manually define the same key on both ends of the communication (in the router or application configuration), but how would that work if two 3rd parties talk together (e.g. you logging in via a personal browser into their banking website)?
This is where asymmetric encryption comes into play, allowing for both ends to set up a secure communication channel while using differing keys.
Asymmetric Encryption
Asymmetric encryption, otherwise known as public key encryption, is based on mathematically related keys, however, at a very high level, utilizes key pairs. One is public, and, as the name suggests, is made available by the entity (e.g. bank website) for anyone wishing to send information. Another is private and only known to the entity (the bank).
A message encrypted with the public key can only be decrypted by the private one, and vice versa.
A simple example of the process is described in the diagram below (courtesy of David Göthberg):
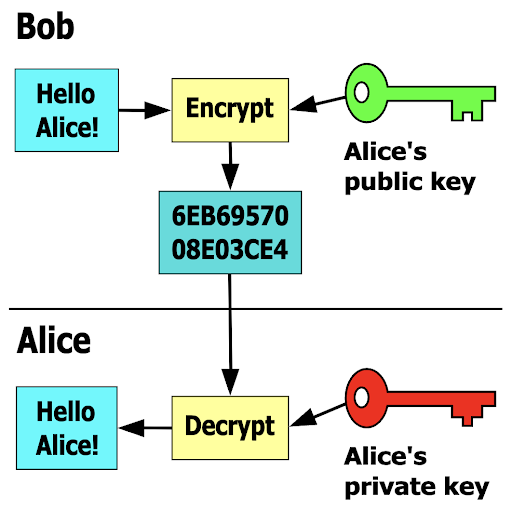
Everyone can generate their own public & private keys, and this is where certificate authorities come into play. They are entities that create trust between sender and receiver, confirming the validity of the public keys. For a user logging into the website, these certificates of authenticity are displayed as a locket in the browser, next to the URL. Any issues with certificates (usually them being expired) are flagged to alert the person that the website might be fraudulent.
HTTP vs HTTPS
A great deal of systems, including CCTV and security, rely on the same methods a website uses to exchange data between the users and devices. For decades, the HyperText Transfer Protocol (HTTP), has been used by machines to exchange the information displayed by web browsers. However, inherently, HTTP is not encrypted.
As the threats from hackers increased, it paved the way for HTTPS (S stands for secure), which is now used for the great majority of websites. Although it might look like HTTPS is using asymmetric encryption, it only does so at the beginning of the communication in order to address the issue of not having a shared key between source and destination. However, afterward, it will resort to using symmetric encryption, utilizing a key exchange inside the established (and encrypted) tunnel.
The reason behind this is solely related to performance: symmetric encryption relies on smaller key sizes than the asymmetric one, and is thus easier to perform.
It is our strong recommendation to utilize HTTPS for any systems you are using. Verkada devices only utilizes HTTPS to transmit data.
For more videos on physical security & networking, follow Dimi on his YouTube channel: https://www.youtube.com/c/DimitrieSanduTech